In October 2013, the management board of GS1 ratified text: EPC Gen2v2. These new features ease the adoption of RFID especially in application areas where the tag carries more information than only its identification. Let’s have a more detailed look at one new key feature of Gen2v2: authentication.
What Does Authentication Mean?
So first of all, what is authentication? A quick Google search resulted with the following definition:
Authentication is the process of determining whether someone or something is, in fact, who or what it is declared to be.
In the RAIN RFID (UHF RFID) context, that something can be either a tag or a reader. In tag authentication, a reader asks a tag to encrypt a message using its stored secret key. If the reader is able to decrypt the tag response, the tag is genuine. This approach can be used to detect counterfeit tags, and as a result counterfeit items. Similarly, in reader authentication, access to a tag is limited to authentic readers. This approach can be used for example in electronic payment solutions. Ken Traub of Ken Traub Consulting wrote a very down-to-earth post about this topic.

RAIN RFID tags that implement cryptographic security are expected to be more expensive than the simplest retail labels. As a result, they will only be used in application areas where authentication gives a significant advantage. Such fields include at least
- Electronic road tolling
- Vehicle registration
- Access control
- Asset tracking and brand protection
- Parking and vehicle authentication
The First Secure Tags and Readers Already Available
In Spring 2015, NXP released the first Gen2v2 tag IC that provides cryptographic authentication, the UCODE DNA. Several tag manufacturers are already providing tags with this IC. On the reader side, upgrading to Gen2v2 requires a firmware update, and at least Nordic ID already has added Gen2v2 support to their readers. So, the technology is available and there seem to be several ongoing pilots that use Gen2v2.
Different Crypto Suites
Gen2v2 is not concerned with which authentication method is used. Instead, the different crypto suites are defined under the ISO/IEC 29167 standard family. For example, NXP UCODE DNA uses the AES (Advanced Encryption Standard, ISO/IEC 29167-10) crypto suite. Some crypto suites may be optimized for low power consumption and quick authentication, whereas others may provide more secure authentication. As new Gen2v2 tags appear to the market, we will most likely also see different approaches to authentication.
What Does Security Mean for RFID Testing?
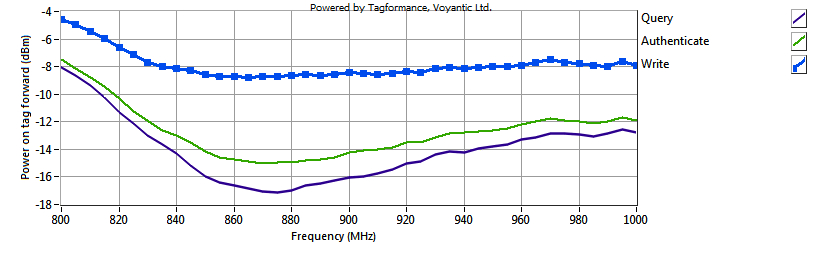
Since Gen2v2 is backwards compatible with Gen2, all Gen2 test methods apply just as well to tags supporting the new standard. The most widely used performance test method for characterizing a tag is measuring its sensitivity as a function of frequency. This reveals both the tuning of the tag as well as the operating range that can be acquired. Typically, the same amount of power is required to identify a tag and to read its memory contents. However, writing to the tag usually takes more power, thus yielding to a shorter write range.

The Gen2v2 security functions introduce a new sensitivity level. The tag’s crypto engine that is required for the authentication may need more power than simply identifying the tag. The figure below shows the sensitivity of a Smartrac Dogbone with the NXP UCODE DNA IC. As the figure shows, authentication needs more power than just identifying a tag, however the difference is only 1 to 2 dB whereas writing the tag memory requires significantly more power.
My company Voyantic delivers test and measurement systems for companies that either develop or use Gen2v2 tags. The Voyantic systems enable companies to reach excellence in tag design and to find the most suitable tag for each application.
If you are interested to learn more, please contact us and let’s talk more!
All blog posts