Tag config memory – What is that? Is it a fifth memory bank? Having configuration words in tag memory is the new normal in the industry and it is slowly gaining importance and cannot be ignored any longer. How did we end up with config words and how can we embrace them instead? Let’s take a look.
Birth of Gen2
The core features and the operating principles of a RAIN tag IC have remained the same since the birth of the protocol in 2004 – The ability to wirelessly read and write memory contents, the ability to lock all or parts of the content from further edits by outsiders, and the ability to permanently disable the transponder when it has served its purpose. That was pretty much it and to a great extent, still is.
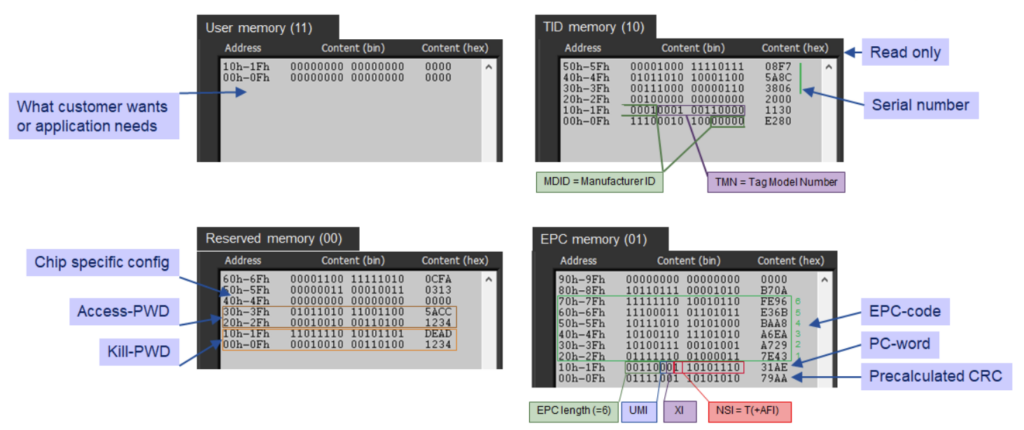
The memory was organized into four parts all with their special purpose. Also, in the air interface protocol, a total of two bits were reserved to specify which memory was to be selected, read, written, or locked.
Memory bank 00 is the “reserved memory” and it contains the 32-bit Kill password as its two first words and the 32-bit Access password for the following two words, four 16-bit words in total.
Memory bank 01 is the “EPC memory”. This is where the EPC code is stored. EPC code is the specified part and length of the memory that will be broadcasted in the inventory process. The two first words in the EPC code have a special function. The very first word has a precalculated error correction word, CRC, stored in it. The second word, referred to as the protocol control word, or PC-word, is an important one. It is a word broadcasted prior to the EPC code in inventory and has several single-bit flags to tell which features tag has activated, and what numbering system it might belong to. It also has a 5-bit L parameter to tell and set the length of the broadcasted part of the EPC code. In short, in the inventory process, the tag would give a reply consisting of PC+EPC+CRC all from this memory.
Memory bank 10 is the “TID memory”. This has all the unalterable records of the tag locked from the factory in the wafer state. In particular, it has MDID specifying the company that designed the IC and TMN specifying the exact IC type and version.
Memory bank 11, is the “user memory”. This is a memory dedicated for the user to write any other entries the application needs, and should contain no special words or bits for the protocol or IC operation. As only a few applications require this type of “disc space” and most applications work solely around the EPC code, most commodity tags don’t actually have any user memory. Manufacturing expensive non-volatile memory “just in case” is too expensive as it uses quite a lot of IC surface area.
Rise and fall of the custom commands
Very soon after the very first wave of ICs had hit the market, the second wave of ICs from roughly 2010 and onward had several new features that were not considered in the original memory organization and protocol. However, the protocol had large RFU provisions for custom commands. So, each tag IC got their own set of special vendor and IC-specific commands to activate and control the new advanced features. The tag features were often clearly documented in datasheets and worked well. However, readers, their command sets, and UIs really struggled to keep up with new and specific firmware versions often needed. For practical matters, like controlling the privacy level of retail tags in this somewhat custom and vendor-specific way just didn’t work too well.
Gen2v2 to the rescue
In 2014, the protocol got a new version, the Gen2v2, which included many of the features added earlier as custom in a somewhat more standard way. The main topics that the new version touched were authentication, encryption, and user privileges. This cleaned the table a little, but still, using new commands to access new features was already found to not always be the easiest solution to adopt.
Configuration words
What happened nearly simultaneously with the release of Gen2v2 was that the control of these added features was slowly transferring from specific new commands to standard Select, Read, and Write commands just pointing to special memory locations. Every reader and reader UI already had filters and memory read functions enabled, so these could be “misused” to control tag settings. Specially formulated Select commands were used to trigger events like “record sensor reading” and “switch to temporary operating mode X”. Writing specific control bits changed settings like tag memory allocations and backscatter levels the state of which could be retained in memory from this point on and to be retained through power cycles.
Soon every manufacturer had their own “config memory bank” or “config word” hidden deep inside the already existing four banks with bits and parameters to be configured to tailor the tag functionality. The trouble was that each IC manufacturer placed the config memory in a different place with varying functionality. Also changing the settings is not always as easy as hailing the tag and writing, as special safety measures are often set in place.
In hindsight, It would have been great to have had a 5th memory bank for tag settings, but as there were just the two bits in each command to specify the memory bank, we were already kind of maxed out at four.
Vendor-specific implementations
Impinj
From roughly the R6 family onwards, Impinj has chosen to place the config word in the reserved memory bank, right after the two passwords at address 0x04. This location has been kept throughout the various R6, M700, and M800 families of ICs with the purpose of each bit being kept more or less similar. Some of the features that can be configured are read range reduction, autotune disable, unkillable mode, and memory split between EPC and User memories, and some inventory optimization modes. More complex ICs like the Monza X-8K have used several words deeper in the same reserved bank for even more settings. Care must be taken when setting the features as only some of the bits can be written, some need to be written from a secured state with a non-zero access password and some bits can only ever be changed once. As the protocol only allows full 16-bit words to be written, changing single bits needs to be done with care and optimally the whole config set on one single write event.

NXP
NXP on the other hand has chosen to primarily use the word at a word address 0x20 in the EPC memory for configuration starting form the Ucode G2iL family of ICs and through the G2iM, Ucode 7, Ucode 8, and Ucode 9. Available features vary from model to model, some of them touching on the topics of product flags, backscatter strength and curve type, parallel encoding, memory config selection, write power indicator, self-adjust settings, and memory checks. Some of the bits are action bits, meaning that selecting on those will trigger special features, some bits are permanent bits for configuring more permanent modes and some are purely indicator bits for reading current feature status. Changing some of the settings is careful work as some require a non-zero access password, then accessing the tag with that, then strictly using a mandatory Write command to perform a toggle-write on the bits that are wanted to be flipped.
EM Microelectronic
EM Microelectronic has been known for their “more involved”, more advanced, and therefore also more complicated ICs hosting a variety of features, such as serial data interface, power outputs, sensoring, IO-pins, NFC+RAIN operation, TOTAL tag talks only modes, etc. These advanced settings often take several words of memory space for configuration in what EM refers to as “System memory” at the far end of the User memory bank.
Alien
Alien has a “Device configuration” often further up the TID memory bank. However, not many public datasheets are available describing the functionalities better. Most probably they are settings performed by the manufacturer and are not meant for the user or an encoding process to mess with. Anyhow, so far four manufacturers and four different memory banks have been chosen for config purposes.
Other manufacturers
With several dozens of Gen2 tag IC manufacturers in the game, there are too many to mention and not all distribute proper open datasheets to share all features in public. However, it seems that some of the newer players on the market have chosen to adopt one of the existing strategies, such as the Impinj Reserved memory word 0x04 for a comparable configuration. This might help existing readers support the newcomers when the location of the settings is the same.
Afterthoughts
There are several good aspects on this topic. First of all, for at least 90% of the customers, the initial settings are just fine. Also, with the two biggest RAIN IC providers on the market covering such a large market share, there nearly are two “standard” ways to control tag configurations. Furthermore, the Gen2v3 is just around the corner (more on that later), but it is not going to touch on the subjects typically controlled by the tag config bits. Unfortunate, that it will not clean this up, but then again fortunate, that it will not introduce even more ways to facilitate configurations that are bound to evolve faster than the protocol versions ever will. The place where the spread and complexity of configuring RAIN tags is putting the most pressure is probably in the encoding of tags where each IC type needs to be recognized and catered for to serve the remaining sub 10% of cases. If your software or UI is not recognizing the IC types, then the datasheet is your friend in deciphering the tag configuration options.
A personal plea to all the RAIN IC manufacturers out there: Please keep the datasheets publicly available to your customers and solutions providers. Also, luckily we are today talking about small single-bit differences in tag configs, as RAIN stands technologically relatively united and nowhere near as spread out and as complicated a disorder as the 13.56MHz playground that NFC is trying to unite and clean up. Let’s continue keeping RAIN united.
All blog posts